With the release of Gravwell 5.0.0, we are also excited to announce the availability of a new kit for logs from Palo Alto's next-gen firewall devices. The kit is still small, but it already provides some useful overviews of a variety of log types and will continue to grow based on customer feedback. This post will touch briefly on Palo Alto's logs and the tools we have built around them.
Palo Alto Logs
Palo Alto's next-gen firewall devices can put out a truly impressive quantity of logs. By default, you'll see traffic logs, similar to Netflow records but containing far more metadata about each connection (114 fields as of PAN-OS 10.2). As you set up additional services in the device, you'll get more: web browsing traffic if you enable SSL Decryption, VPN connections, Wildfire malicious file analysis, and so on.
The logs can be exported to Gravwell via syslog (see https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/monitoring/use-syslog-for-monitoring/configure-syslog-monitoring) fowarded to the Gravwell Simple Relay ingester. Detailed configuration instructions are included in the overview playbook within the Palo Alto kit.
Logs arrive as CSV embedded in a syslog message, a format covered in a previous blog post:
794 <14>1 2022-04-01T10:06:58-07:00 PA-VM - - - - 1,2022/04/01 10:06:58,4151AF56B2F71F4,TRAFFIC,
end,2561,2022/04/01 10:06:58,10.150.100.1,1.1.1.1,10.150.0.100,1.1.1.1,Trust-to-Untrust,gravwell,,
web-browsing,vsys1,Trusted,Untrusted,tunnel.10,ethernet1/1,Gravwell,2022/04/01 10:06:58,218,1,
46704,443,37349,443,0x1400019,tcp,allow,7316,483,6833,4,2022/04/01 10:06:50,0,all-urls,,
7081676986862534840,0x0,10.0.0.0-10.255.255.255,Australia,,1,3,aged-out,0,0,0,0,,PA-VM,from-policy,
,,0,,0,2022/04/01 10:06:50,N/A,0,0,0,0,ef59c03c-8fe5-4a52-893b-0015ca66af4f,216,0,
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,2022-04-01T10:06:58.241-07:00,,,internet-utility,general-internet,
browser-based,4,"used-by-malware,able-to-transfer-file,has-known-vulnerability,
tunnel-other-application,pervasive-use",,web-browsing,no,no,0
The meaning of each field is defined by Palo Alto, of course, but correlating them by hand is difficult. Luckily, our new kit makes parsing logs much easier by including auto-extractors.
Keystone Functionality: Auto-extractors
Auto-extractors tell Gravwell how to parse data in a given tag. By shipping predefined auto-extractors for the various log types, the Palo Alto kit lets you pull any given field out of a log with ease. If we run `tag=gravwell ax` and expand one of the entries returned, we can see the huge list of fields it extracts automatically: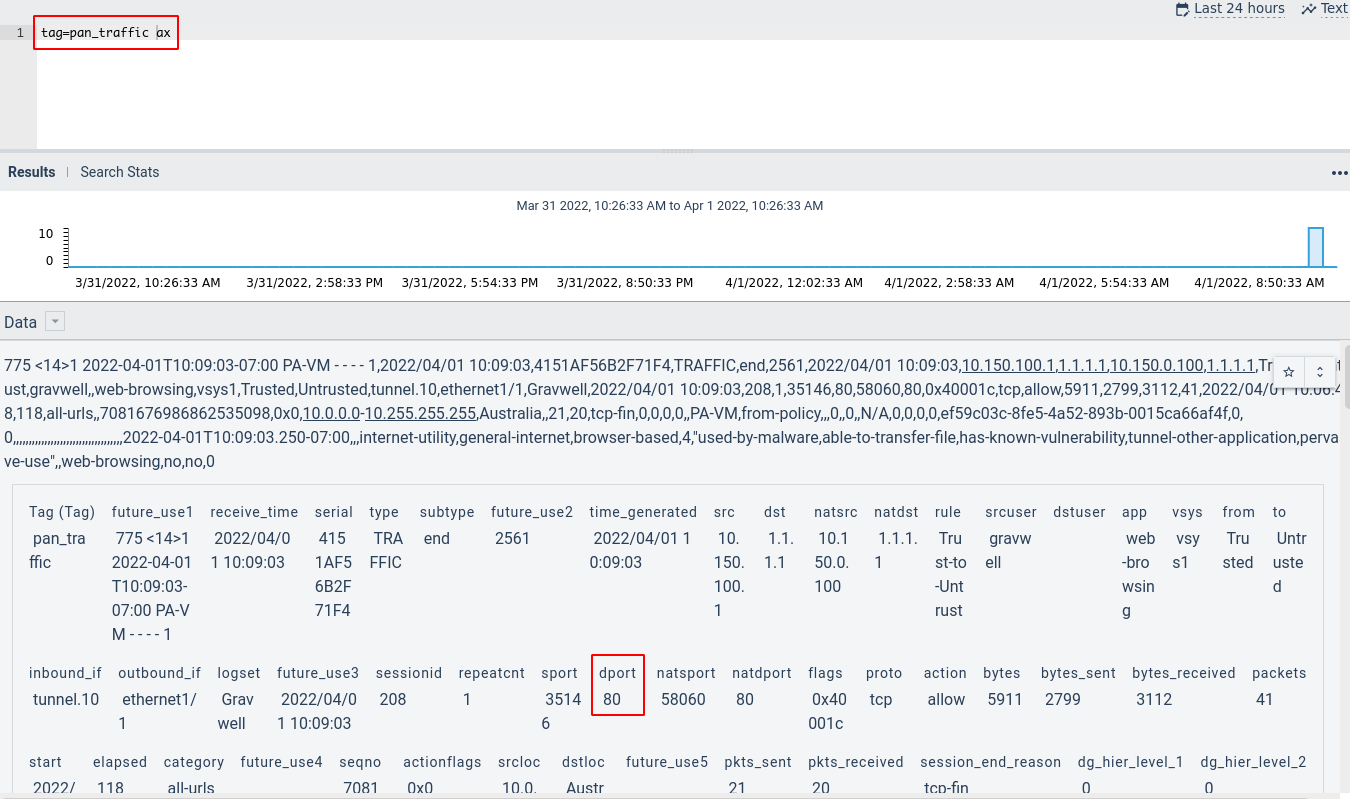
After we pick a field of interest ("dport" aka "Destination Port", for instance), we can start to filter our queries based on that: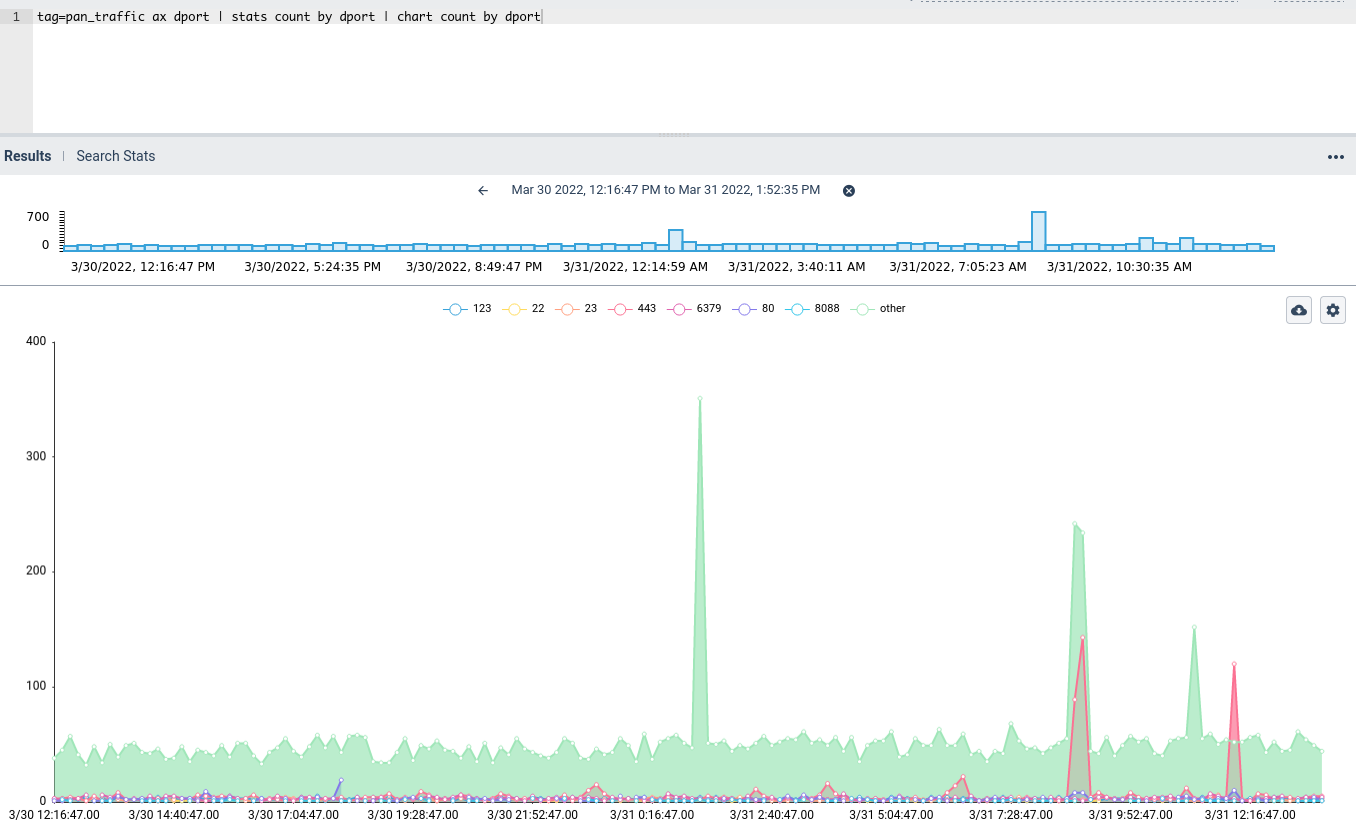
Dashboards
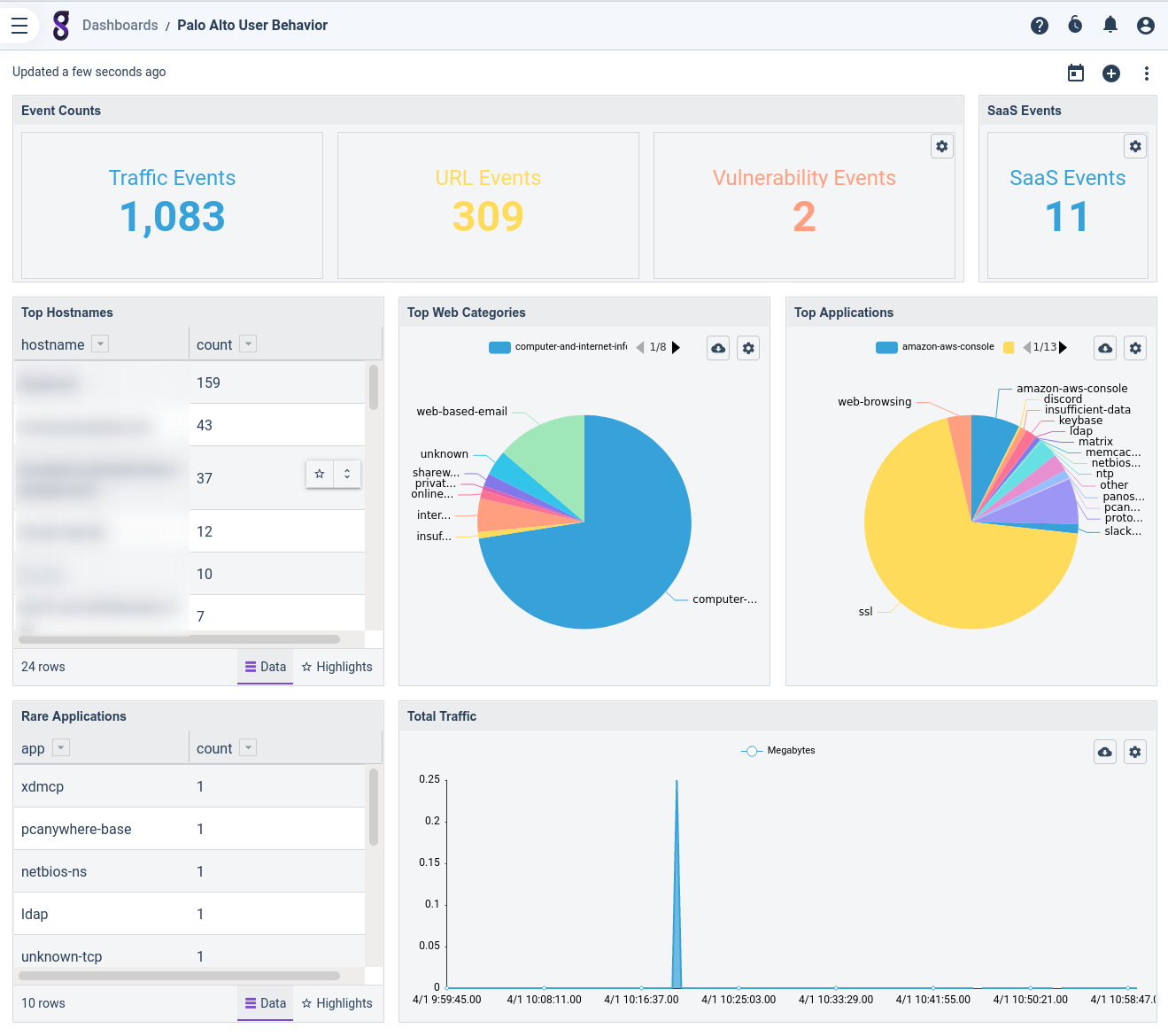
Although the auto-extractors are an essential enabler for working with Palo Alto logs, the best entry point for analysis is the set of pre-built dashboards we include. The kit currently ships the following dashboards:
- User Behavior: a high-level overview of logs generated by user activity.
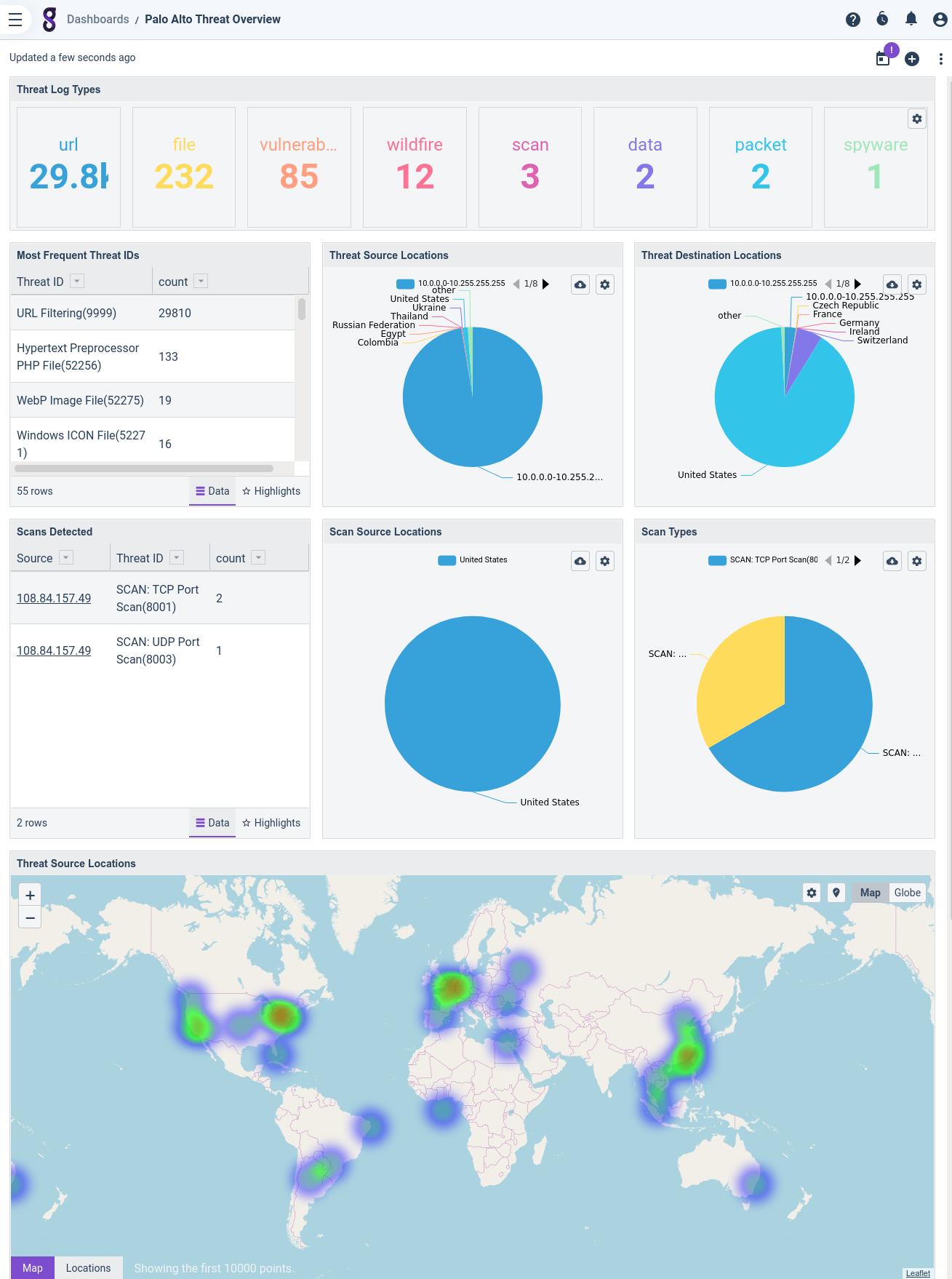
- Threat Overview: an analysis of various observed threats.
- Wildfire Overview: information about potential malware submitted to the Wildfire service for analysis.
- SaaS Overview: see what sort of SaaS applications users are accessing.
- GlobalProtect Overview: stats and logs related to the GlobalProtect VPN service.
- Config Overview: info about config changes on the Palo Alto device(s).
- Threat Investigation: find threats related to a particular IP address (see Actionables section, below).
Actionables
Actionables are powerful tools in Gravwell which allow you to click on search results and pivot into other dashboards or queries for further investigation. Here's a slightly contrived example that uses both the Zeek kit and the Palo Alto kit: Suppose I decided to browse my Palo Alto threat logs and got curious about a suspicious-looking URL, "www.gravwell.io". I can click on that name within the log to bring up a list of actionables: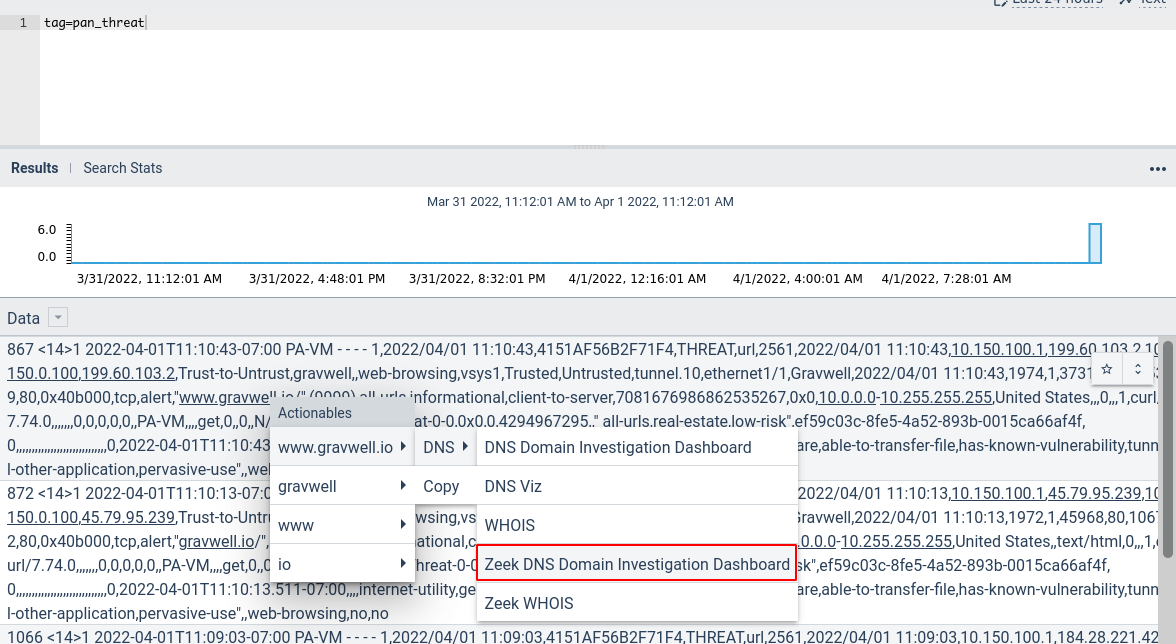
I then select the Zeek DNS Domain Investigative Dashboard to get more information about the hostname, learning which hosts have queried that hostname and what IP addresses were returned for "www.gravwell.io":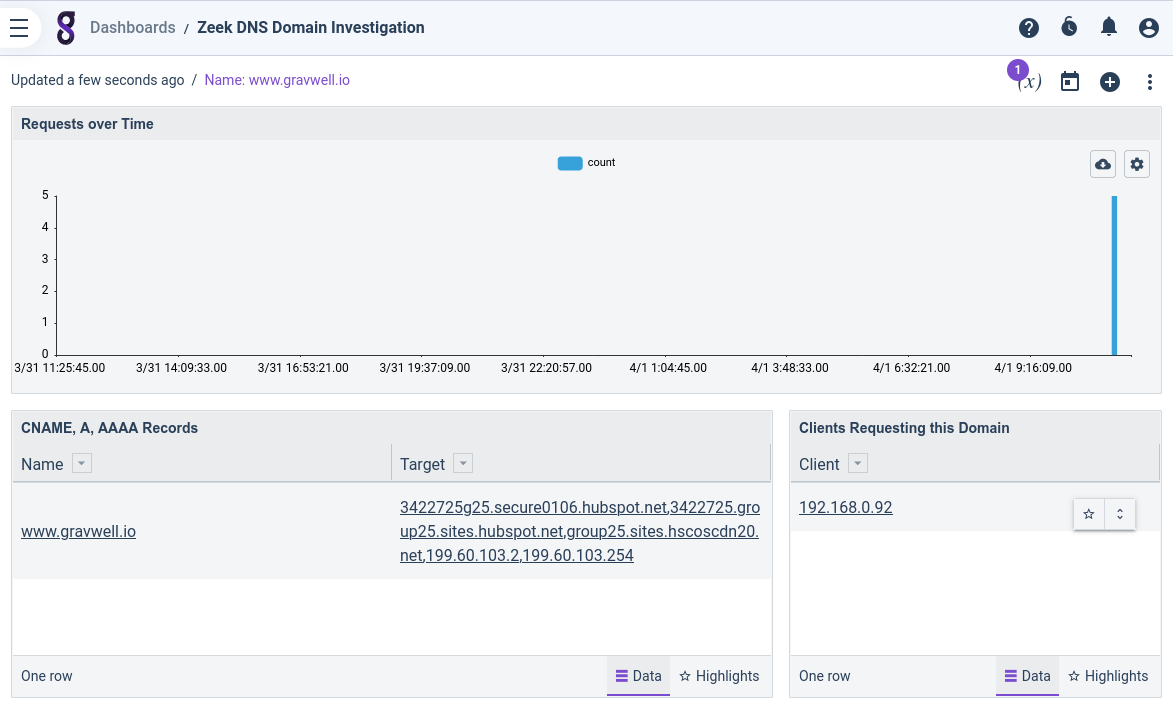
From within *that* dashboard, I can then click one of those IP addresses and open the Threat Investigative Dashboard from the Palo Alto kit: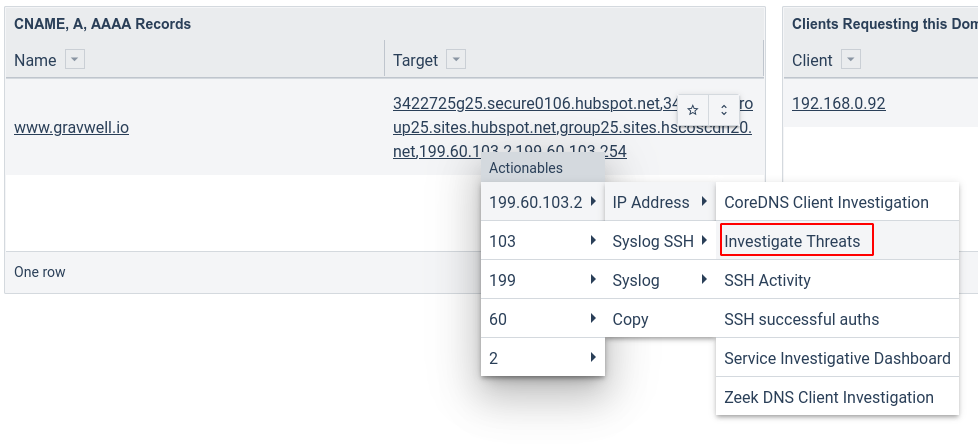
I am reassured to see that the IP address seems pretty benign: the only threat logs related to it are of the "URL" type, and it is categorized as "general-internet". Because I have my Palo Alto device set up to log *every* URL, even completely benign ones, I feel pretty confident that "www.gravwell.io" is ok.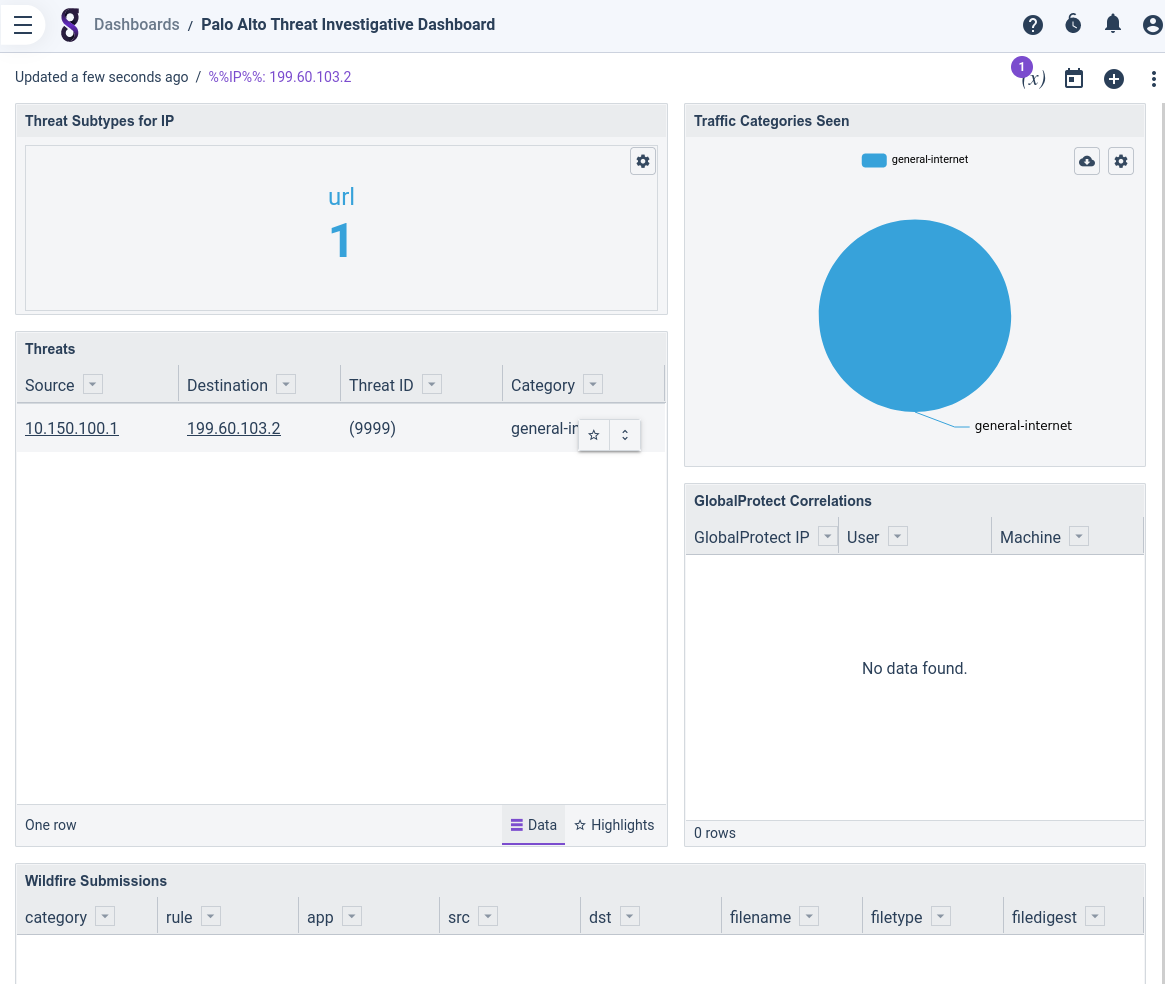
Conclusion
We hope our new Palo Alto kit provides the springboard Gravwell users need to start getting a handle on their Palo Alto logs. We encourage anyone with a Palo Alto device to start forwarding their logs into Gravwell and play around with the kit; each dashboard is full of queries which can serve as examples and starting points for further investigations.
If you want to get logging under control with Gravwell, check out our free Community Edition!
Lastly, if you have any questions about this recent kit and want to ask the team, join our discord below:
John's been writing Go since before it was cool and developing distributed systems for almost as long.
